SCIENCE + TECHNOLOGY
Utah is prepared to handle different types of cyberattacks
May 12, 2021, 10:35 PM | Updated: May 13, 2021, 10:33 am

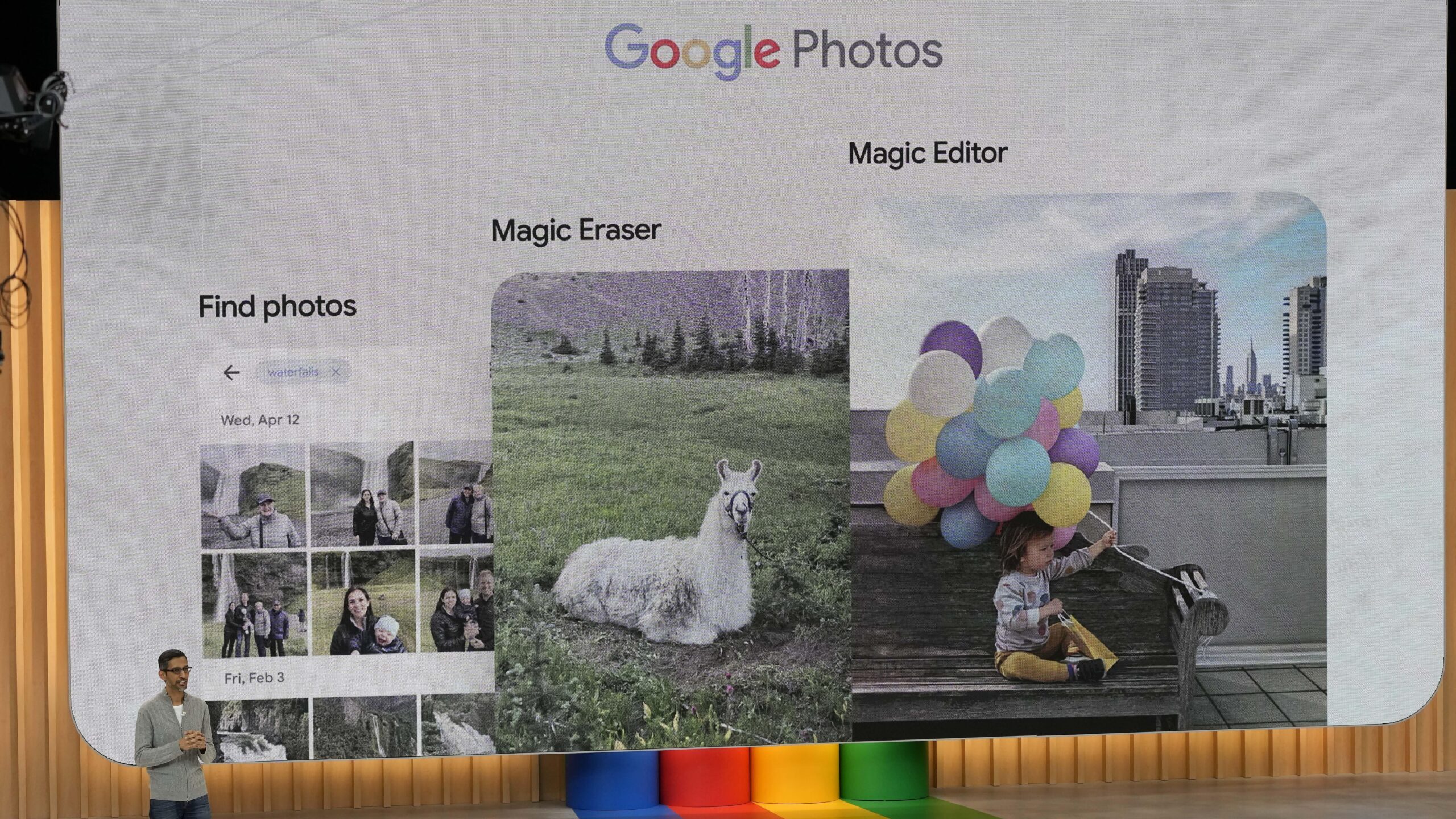
Signage is displayed on a fence at the Colonial Pipeline Co. Pelham junction and tank farm in Pelham, Alabama, U.S., on Monday, Sept. 19, 2016. Customers buying gasoline at grocery stores and other independent retailers may pay more than those shopping at name-brand outlets after the biggest gasoline pipeline in the U.S. sprung a leak in Alabama on Sept. 9. Colonial Pipeline Co. has proposed restarting the line on Sept. 22, according to the Alabama Emergency Management Agency. Photographer: Luke Sharrett/Bloomberg via Getty Images
The Colonial Pipeline which provides gas from the Gulf Coast to the Northeast, restarted Wednesday. On Friday, a cyberattack took them offline affecting some of its information technology systems.
The nature of the cyber attack is unclear, according to the Associated Press, including who launched it and what the motives were.
Join me as I give an update on the Colonial Pipeline incident. https://t.co/y3bWsnUnBp
— President Biden (@POTUS) May 13, 2021
Chris Parker, the Director of the Division of Public Utilities for Utah, explained “some of the actual shutting down of the pipeline was preventative.”
“It wasn’t that the hackers shut the pipeline down themselves. It was that they saw the hackers in the system, and the company went and shut the pipeline down to avoid problems,” Parker said.
Parker reassured Utah would not be affected even if the pipeline remained offline longer.
“We are pretty well isolated from that in terms of price as well as actual physical supply,” Parker said.
Utah takes steps to prevent cyberattacks
According to Parker, utility companies in Utah employ different kinds of protections against cyberattacks. The state’s utilities provide annual briefings to the Division of Public Utilities about their cybersecurity process and plans.
Companies like Rocky Mountain Power and Dominion Energy have systems in place to guard their data as well as their physical security, Parker confirmed. “They have layered defenses so the network that they have internally, only some of it is connected to internet-based systems,” he said.
Companies like these spend a lot on securing all identities in the organization, so the individual logged in is actually who they say they are. This “identity security” helps them protect their data as well as their systems.
Utah’s utility companies do extensive inspections of both the individual’s and company’s accounts. Parker explained that these are not financial audits but “…tests to see what might be compromised and what you might do in the event of a compromise.”
Different types of cyberattacks
Colonial’s hack was a ransomware hack which, in a nutshell, is “pay us enough and we’ll get out.” Parker discussed the different kinds of cyberattacks Utah’s utility companies protect themselves against.
In addition to ransomware attacks, they are concerned with data theft, denial of service attacks and the broader concern of terrorism. “The vast majority of these attacks get in through phishing attempts,” Parker said.
Phishing attempts often look something like an email that says you need to update your password, click here, but if you click there it lets the hackers in because the email is not really from the company it purports to be from.
For example, CNN reported a Texas school district lost $2.3 million in a phishing email scam according to officials.
According to Parker, Utah’s utility companies have “employed internal fake phishing attempts to identify the vulnerabilities in their companies. ” For example, the companies will send a fake email to 10,000 of their employees and if 500 of them fell for it they have education sessions.
“We would go to those 500 employees and say, ‘Hey guys. Take this special class, and if you fall for this again, you might get disciplined,'” Parker said. They have sophisticated systems that are not just fortifying the networks themselves but changing the human behavior that is often the main vulnerability.
Parker is less worried about the larger utilities like Dominion Energy and Pacificorp. The damage that can be done with those utilities is much greater, but the likelihood that it will happen is much smaller because they have more robust systems in place.
“I worry about the smaller utilities that are run by less sophisticated parties. The hacker bang for the buck is also diminished, so we’re lucky in that regard,” Parker explained.
“The challenge,” Parker believes, “is you can spend as much money as you want to on this stuff and still have vulnerabilities because it’s ever-changing.